- November 30, 2022
- Catagory Managed IT Services
Your Security Strategy Should Include MDR
Implementing security technologies such as a Security Information and Event Management (SIEM) platform will only protect your organization if they are effectively managed, which is why you must consider embracing managed detection and response (MDR).

MDR isn’t a technology, it’s a service with SIEM acting as key pillar of its foundation, as well as endpoint detection and response (EDR). Delivered by a third-party service provider, it allows you to tap into cybersecurity expertise that’s in high demand and difficult to attract and cultivate internally. Your managed service provider (MSP) is a great resource for accessing MDR and a team of skilled professionals who can help you manage and optimize your security.
It’s also more proactive – security experts on staff with your service provider leverage SIEM and EDR to monitor and analyze events so they can identify dangerous threats before they can have a negative impact on your business. MDR delivered by an MSP is better able to keep up with volume of anomalous events to discern whether they will result in a serious data breach or malicious attack by a threat actor.
The most compelling reason to seek out a service provider who can deliver MDR is they can do it 24 hours a day, 7 days a week, 365 days a year. For most small and medium sized businesses, it’s simply mot feasible to staff your IT team with security experts all the time, including holidays. Even if you can attract the skilled personnel, it’s better to have them focused on more strategic IT and security initiatives. An MDR provider reduces the burden on your own people, so they have more time to breath, given all their other responsibilities.
An MDR analyst with the latest and greatest tools can better sift through the vast amounts of data being ingested from different sources and endpoints and analyze it. They are also able to understand how to automate security tools to work more effectively so they’re only handling incidents that require human intervention. Their ability to interpret data not only helps them prevent and mitigate vulnerabilities, but also prevent future attacks by applying lessons learned to make your organization more resilient.
A managed service provider is best equipped to optimize security platforms including SIEM and EDR as part of an MDR solution because they can better access and scale these advanced security tools and the necessary skilled professionals capable of using them effectively.
- October 27, 2022
- Catagory Managed IT Services
Your Printers Need Good Cybersecurity, Too
Today’s smart printers must be protected like any other endpoint in your organization – because most printers today are multi-function devices with onboard storage and are part of your office network, threat actors see them as a prime target.
If you’ve not thought to include your printing infrastructure as part of your overall security strategy, now’s the time – and your managed service provider can help.

Believe or not, your printer is one the most vulnerable endpoints on your network, and a hacked printer will at the very least inconvenience your users and possibly threaten your entire business. In the same way that an employee smartphone or remote worker’s laptop is a gateway to mission critical systems and information on your enterprise network, your fleet of printers represent computing endpoints that can be hacked.
Just as people used to send funny jokes via fax machines, networked printers are now the target of pranks, with hackers infiltrating through open printer ports to execute bogus test page with messages on them to let the organization they’ve been breached. More extreme examples involve hackers using unsecured printers to spew out ads and random documents no one your company wants – and wasting paper is the least of your worries.
If your networked printer gets hijacked, you should be as alarmed as if your laptop screen was suddenly filled with pop up ads. And just like your laptop – or smartphone – a printer is a great jumping off point for threat actors to sneak into your office network while your users are distracted by failed print jobs.
You may not even get any indication your printer has been compromised. Rather than bother with silly pranks, a serious hacker will use their access to move around your network until they find a way to do serious damage by stealing data or holding it hostage with ransomware. Before you realize it you’ve been compromised, it may be too late to prevent damage to your business and reputation.
But like any endpoint, a network printer can be secured by following protocols that prevent them from being accessed remotely or by unauthorized users. A managed service provider can help you audit and secure your printer fleet as part of a broader strategy to secure your IT infrastructure.
- April 28, 2022
- Catagory Managed IT Services
How an MSP can help secure your business
Many businesses turn to a managed service provider (MSP) to solve a specific problem but may not always be aware of the breadth of capabilities their MSP has to offer, including security.

The cloud is a great enabler of many of these services, and it allows you to scale up your security protections as needed without a great deal of capital investment or dedicated IT staff. Because your MSP is helping multiple businesses with their security needs, they benefit from economies of scale and so do you. They are also able to keep pace with trends in IT security, whether it’s available tools, best practices, or new threats, and apply them to the security services they offer you.
If you’ve not fully explored what your MSP has to offer, you should consider evaluating your security posture and looking additional capabilities they have to offer.
Cloud backup and disaster recovery
Whether you’re the victim of a cybersecurity attack, data breach or natural disaster that disrupts your primary systems, having a disaster recovery and backup strategy protects your assets, saves your critical and confidential data, and keeps your business running even after your network is compromised. Backup was one of the first services to move to the cloud, and if there’s one service you should outsource to an MSP, it should be cloud backup and recovery – your MSP can step in quickly if you need to restore your primary system so you can keep your employees productive and your customers happy.
Network security
Your network is comprised of servers, computers and other hardware, and software applications, and your company’s data flows through all of them. Without it, your employees can’t share information or communicate. Not only will a data breach or cyber attack impair your ability to operate, but they could lead to revenue loss, regulatory consequences, and damage to your reputation. Your MSP can help defend your network endpoints, including desktops, laptops, and mobile devices, and provide high-quality help-desk service.
Penetration testing
A penetration test (“pen test”) evaluates the security of your IT infrastructure by safely looking for vulnerabilities. Your MSP will try to systemically compromise servers, network devices and other potential points of exposure, and then report back with their findings and recommendations. A pen test can act as an audition for MSP to demonstrate they can find problems, help you remediate any issues, and implement ongoing security services they can manage for you.
Proactive 24/7 monitoring services
Even without a cyberattack, network infrastructure can falter. Your MSP can provide real-time monitoring of organization’s network infrastructure and act immediately any issue that arises with instant troubleshooting to avoid disruptions to workflows and business operations. Around-the-clock monitoring maximizes business uptime, prevents performance or service interruptions, and provides peace of mind that your network is safe and sound.
If you’re concerned about your security posture but don’t know where to begin, your MSP should be your first call. And if you don’t have one, selecting one should heavily depend on their ability to show how well they evaluate your infrastructure, their recommendations to secure it, and references from other customers who’ve enjoyed uninterrupted operations as one of their customers.
- December 11, 2019
- Catagory Managed IT Services
Be Mindful of Technology Trends for the Coming Year
Even as 2019 starts to wind down, it’s hard not think about the year ahead and how best to focus our energies—including IT operations. It’s safe to say the more things change, the more things stay the same as many of challenges will continue into 2020 as they have in previous years.

However, these challenges continue to evolve and coming up with a strategy for them can better prepare you for emerging technologies and trends that are bound to affect your business operations and your IT infrastructure, if sometimes only indirectly.
Security
It seems a little obvious to say security is important—most consider it table stakes when deploying and managing IT today—but it can never be overstated that it’s something you must keep on top of. Threats to data and applications, either from human error or malicious threats such as malware and hackers, are never going to go away. If you only make one New Year’s resolution, make it to get your arms around security. The next year will go smoother operationally with better visibility into what’s going on across your network, and what’s happening to your data. Both your C-suite and customers will benefit.
Compliance and Privacy
Security should not be confused with compliance and privacy, and vice versa, but all three are heavily intertwined. Security is an essential part of being compliant with privacy legislation, and there’s consequences for not being able to adhere to the various regulatory frameworks and legislation in play. The European General Data Protection Regulation (GDPR) and Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA) aren’t going anywhere, and the state of California has its own privacy legislation in the works. Despite their countries of origins, their impact can penetrate many other jurisdictions worldwide. If you don’t know if and how these and other rules affect you, make 2020 the year you figure out for certain.
Data Governance
Part of compliance is data governance, but even without privacy legislation at play, there’s plenty of reasons to have a strategy in place to manage the exponential growth of information. Whether it’s practical considerations such as storing it cost effectively or making it better available for business applications, the time to get a handle on your data is always now because it’s only going to grow in volume and velocity.
Multi-cloud
As public clouds platforms proliferate and widen their scope to offer more services and handle more workloads, a multi-cloud model has emerged that reflects the reality that business requirements from various cloud platforms differ. Some are better suited for handling the application and data demands of marketing and salespeople, while others are better geared for processing a high volume of transactions, rapidly and reliably. Although a public cloud provider may do everything a business needs, it can also mean compromising on features or performance. A best-of-breed, multi-cloud approach reduces dependence on any single public cloud platform while preserving the flexibility to move workloads between providers.
Business Intelligence and Data Analytics
Getting a handle on your data is essential if you want to make good use of it. No matter than size of your organization, it’s full of information that can help you optimize operations and business processes while improving your marketing, whether it’s by helping you land new customers or keep the current ones happy—even upselling them to buy more of your products and services. Business intelligence certainly isn’t new, but because every organization is swimming in information, it’s no longer a luxury. If you’re not tapping into it for competitive advantage, others in your industry certainly are.
The Internet of Things / Operational Technology
Some of that data is coming from new and interesting place as the Internet of Things and operational technology (OT) devices are increasingly comprising enterprise networks. Traditionally segmented from IT infrastructure, OT endpoints in manufacturing and municipal facilities that deliver water and power are being added to existing IP networks. These pose challenges from a management and security perspective, but also present opportunities to innovate based on the data that’s ingested, as well as optimizing business processes.
Automation
Gone are the days of throwing more people at a problem. Even if money is no object, it’s no longer feasible to do every task manually—people just can’t keep up. In the rush to try, human error can lead to misconfigurations that impact security posture, compliance and the customer experience. It means your IT teams aren’t focusing on strategic initiatives and you’re not focused on your core business. Whether it’s automating through emerging technologies enabled by artificial intelligence or handing off repetitive tasks to a business process services provider, you need to make smart decisions about who does what and why.
A new year always brings new opportunities and new challenges. No matter the size of your business or industry, all these technology trends are bound to affect you in some way. Understanding how is the first step, and that’s where a managed IT services provider can help. They’ve already helped other customers navigate the terrain and develop best practices that you can implement to move your business forward and improve the bottom line.
- November 7, 2019
- Catagory Managed IT Services
IT strategies for SMBs should include a managed services provider
IT strategies for SMBs are essential for organizations looking to scale and up grow their bottom line, but many face the same challenges as large enterprises without the resources.
There are ways to do what the bigger players are doing so you can grow your organization and your profits, but IT strategies for SMBs must have a vision, an understanding of the cloud solutions available to them, and consider how a managed services provider can get them were they need to be within their budget.
IT strategies for SMBs start with an audit

Not all businesses are the same, so IT strategies for SMBs will vary by industry and inherent regulatory frameworks, business models and overall digital maturity. Regardless, there will be low hanging fruit that can advance the organization quickly and affordably, while other initiatives will be multi-year projects that must to be broken down into achievable milestones.
Common goals within many IT strategies for SMBs are tapping into needed talent, which could involve recruitment and retention of employees or selective outsourcing to access skills on demand, improving agility by automating tasks or handing them over to a business process services organization. Given the ramifications of data breaches, bolstering security should also be a priority and embedded within all growth activities. It also might be achieved with automation—even artificial intelligence—or turning to a managed services provider for help. Most organizations are looking at how they can improve overall productivity.
IT strategies for SMBs should identify priorities based on a comprehensive audit of your environment, whether it’s your own on-premise infrastructure or cloud deployments, including use of the public providers. You can’t have a vision of the future without knowing for sure where you are today. This assessment is also something that can be done in collaboration with a managed services provider and can clarify your current security and compliance posture.
There are solutions in the cloud
Your IT audit can help you easily identify what you can do by yourself and what elements of your strategy are better executed with the help of an experienced technology partner.
There are number of solutions available with IT strategies for SMBs in mind. You might begin by implementing organization-wide, online collaboration with Microsoft Office 365 and Teams, or alternatively, go the Google route with Gmail for business and Docs. You’ll want to think about the value of consolidating solution providers as simplicity for SMBs can keep costs under control and ease user adoption. Even if you go best-of-breed, most cloud-based SMB solutions are pay-as-go so you can budget expenditures as you grow.
No matter what solutions you adopt, remember they’re only as good as the workflows and processes you foster and the underlying infrastructure that supports them. In case of the latter, it’s one of the first things you should consider handing off.
Leverage the investments of a managed services provider
As much as any SMB requires technology to operate and is just as driven by data as its larger counterparts, they’re not in the IT business. And just as cloud-based SMB solutions are pay as you go, managed IT services providers offer similar pricing flexibility and can scale up and down in alignment with the ebbs and flows of your business.
Once you’ve done an audit to understand where you are and where you’re going, you can figure which problems are best solved by a managed services provider, even if it’s only one business process, but one of the biggest benefits is you no longer need worry about maintaining aging infrastructure with the limited IT staff and resources you have. A managed services provider has made the investments and is committed to maintaining their infrastructure to support your applications and store your data with a high level of security.
This investment isn’t limited to hardware and software. Often, an SMB can’t justify bringing on talent full-time, such as a DBA, but a managed services provider can provide people on demand as needed so you don’t have to worry about recruitment and retention but still enjoy necessary expertise when you need it.
IT strategies for SMBs are all about a better bottom line
Embracing cloud solutions and entrusting data and business processes to a managed services provider are key elements of IT strategies for SMBs, even if it’s only for a small segment of daily operations. The right combination can improve productivity and the speed of your service delivery at a lower cost, and most of all, lead to a better bottom line.
Sanjeev Spolia is CEO of Supra ITS.
- August 22, 2019
- Catagory Managed Cloud Services
Ready to mix and match with multi-cloud?
Hybrid cloud environments are constantly evolving and today one cloud is no longer enough—diverse workloads mean you must be ready to embrace a multi-cloud model.
Whether it’s one, two or more of the public cloud such as Microsoft, Amazon, Oracle or Google, or turning to a managed IT services provider to help you leverage economies of scale, it’s likely you’re already facing the realities of multi-cloud, including the benefits and the challenges.

What is multi-cloud?
A hybrid cloud brings together an on-premise data center (a private cloud built on cloud technologies) with a public cloud, while multi-cloud brings together multiple cloud services from different providers, both public and private. In the same way organizations might have chosen a best-of-breed approach to their on-premise applications deployment, the multi-cloud paradigm allows for the selection of the best cloud provider for a given workload.
The multi-cloud model is driven in part by open source and the desire for organizations to leverage cloud technologies to best serve customers, suppliers, partners and even employees. Further accelerating the momentum of the multi-cloud is the ability to run services from providers such as Microsoft and Amazon Web Services (AWS) in a private data center thanks to Azure Stack and AWS Outposts. Add the ability to run VMware on AWS, and organizations can mix and match cloud services as much as they want to meet the specific requirements of any given workload.
The right cloud for the right workload
Like the best-of-breed approach to on-premise software applications, multi-cloud offers many benefits, including the ability to pick the right tool for the right job on a case by case basis, rather than just one provider that may excel on one capability while lacking robustness in others.
Similarly, it allows you to avoid being locked into a single cloud provider and take advantage of innovation from a variety of vendors, while also enjoying the flexibility and scalability you need as your business grows and your needs evolve. A multi-cloud strategy also gives you some measure of control, including cost governance, as public cloud strategy can sometimes cost more than a private cloud approach, depending on the workload.
More clouds, more challenges
Running a multi-cloud environment is not without its challenges, however. Not all clouds are equal and not all providers do things the same way. AWS and Microsoft Azure might offer the same service, but have different processes, so what the customer is responsible for on their side may differ depending on the provider.
Using a mix of cloud providers can add even more complexity to compliance and security too. Not only do you have to worry about your own data center being compliant with industry standards and regulatory frameworks such as privacy legislation, but you need to be certain your providers are up to snuff too by understanding all compliance requirements and creating the necessary policies.
While cloud providers may tout their security features, you still need to have the right in-house resources to manage application and workload security in a multi-cloud environment, which makes identifying and containing security threats even more complex. This includes securing connectivity across the multi-cloud environment—after all, data is the lifeblood of your business, and a multi-cloud environment means mean you need to securely and cost-effectively move data between one cloud provider and another, as well as to and from your own data center.
Get help with multi-cloud management
If you’ve already embraced the hybrid cloud, you’re in a good position to take advantage of multi-cloud. But as with all IT infrastructure demands, there’s a lot to be said for tapping the expertise of an experienced managed service provider to help you with some of the heaving lifting. They already have solid track record of managing, securing and optimizing multi-cloud environments, which enables you to focus on strategic initiatives without add more to your plate.
- March 7, 2019
- Catagory Managed IT Services
A Good Disaster Recovery Plan Has a Team in Place Before Disaster Strikes
Recovering from any disruption requires the right people. When it comes to disaster recovery plan, success will depend on quickly mobilizing a team to maintain business uptime.
Every user in your company can be affected by an incident that is escalated to a disaster. By identifying people you will need to quickly restore operations as part of your planning, ideally your customers won’t be affected because you’ll be able top to bounce back quickly and minimize the disruption to business operations.
Keep disaster recovery reflexes sharp
Your disaster recovery plan should include a management team that takes on the critical responsibilities and decision making, starting with whether the disruption is in fact a disaster.
If it’s concluded that the incident is severe enough to meet the criteria, your disaster recovery team must mobilize and do the following:
- Manage and coordinate the disaster recovery plan
- Activate other staff in the organization, as well as your service provider, in priority—some people may be needed immediately, while others need to be on standby depending the role in the plan
- Ramp up any alternate facilities and secondary sites
- Review the recovery procedures to be activated that will support your recovery objectives
Who should be on the team?
There are several key roles that should be already be assigned by your disaster response management plan before a disruption occurs.

Your information security group should always be represented on your disaster recovery team, as they have specific, specialized responsibilities, including a review of the recovery goals, understanding the magnitude of the damage, and making sure information security procedures are followed by the disaster recovery team. They can also assist with the preparation of an accurate news media statement that outlines a description of the incident, how and when it happened, and who will be affected and how.
Other team members include a disaster recovery coordinator to liaise with your service provider and any vendors that might contribute to the affected infrastructure. Their job should also be to set up a schedule for status updates throughout the recovery process right up until full restoration.
Another important role you must fill is that of a disaster recovery crisis manager, whose job it is to keep everyone informed on latest developments and be a single point of contact for all team members. They have several critical responsibilities, including:
- Making sure all users and are familiar with the disaster recovery management plan.
- Provisioning additional telephone lines for extra staff if needed.
- Getting a snapshot of activities in progress when the disruption happened from the information security team, an estimate as to how long these activities will be delayed, and when the next update can be expected.
- Developing a public statement approved by disaster response management team that can be distributed to everyone affected, including customers and users, as well as media. Multiple statements may be required, including one when the recovery operation is done, and regular business activities have resumed.
Having a well-thought disaster response management plan in place will only be effective if the right people there are to executive as soon as the alert is sounded. You should frequently revisit your plan to confirm the people assigned to these critical roles understand their responsibilities and that they are still available should disaster strike.
If you haven’t begun to think about disaster recovery planning or feel your plan needs an update, check out our Disaster Recovery Primer.
- February 22, 2019
- Catagory Managed IT Services
Prime Yourself for Disaster Recovery to Maximize Business Uptime
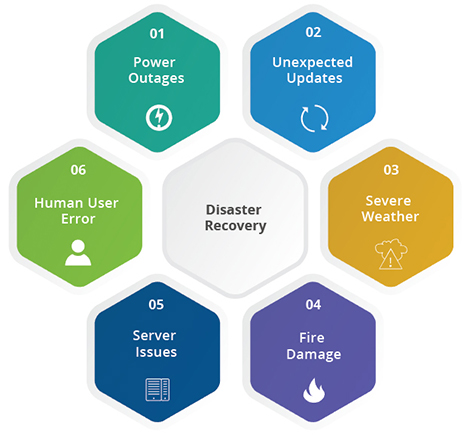 Every organization today is data driven, regardless of size, and it’s just a matter of when, not if, that data is put in jeopardy. For small and medium-sized business with resource and IT infrastructure constraints, it can seem an overwhelming challenge to prepare an effective disaster recovery plan and maximize business uptime.
Every organization today is data driven, regardless of size, and it’s just a matter of when, not if, that data is put in jeopardy. For small and medium-sized business with resource and IT infrastructure constraints, it can seem an overwhelming challenge to prepare an effective disaster recovery plan and maximize business uptime.
The good news is that cloud computing allows smaller organizations to enjoy the same peace of mind large enterprises have with the help of an experienced technology partner who help you lay out at plan of action when disaster strikes.
What you should expect from a solid disaster recovery plan
The point of any disaster recovery plan is to make sure there are steps in place to restore any mission critical applications and data after a disruption. It outlines all the all the activities, resources and procedures in the event of a disaster so you can ensure business uptime and return to normal operations as quickly as possible in the event of a disruption.
It starts by notifying everyone who needs to be part of the solution that there is a problem, whether it’s company staff or resources at your service provider, and outlines who’s responsible for what. Once the process is underway, the recovery phase should enable you to restore temporary operations and repair any primary system damage. There’s a lot that needs to happen during the recovery, and an effective disaster recovery plan will coordinate and facilitate communication between all parties involved.
Mapping the connections
There’s also a lot of moving pieces that must be considered. A disaster recovery plan should identify the processes that are in scope, who is responsible for those processes and all the interdependencies affected by the disaster.
Dependencies will help establish the severity of the disaster—one single glitch may be just that or could have a much broader impact on business operations. When a single resource becomes unavailable, it affects many user and customers, and disrupts multiple business processes. Here are some examples of dependencies your disaster recovery should keep in mind:
- Reporting and analytics: Collection, logging, filtering, and delivery business data to relevant stakeholders may stop working and the user interface layer may or may not be also affected.
- Interfaces: Users at all levels, including administrators, may be blocked from accessing software and systems, whether it’s on the client or server side, through web interface or downloaded application.
- Networking: Connectivity to necessary resources could be slow or disappear completely. compromised and/or significant latency issues in the network exist that result in lowered performance.
- Storage: Even if your connectivity and applications are functioning, the failure of a storage resource such as storage area network (SAN) could block access to a handful of files essential for running the business.
There are many more dependencies, and your service provider is well-equipped to help you identify them so you can quickly resolve issues and take advantage of secondary infrastructure in case of an interruption that has a broad impact on your business.
If you haven’t begun to think about disaster recovery planning or feel your plan needs an update, check out our Disaster Recovery Primer.
- January 25, 2018
- Catagory Hybrid Cloud
Ready to take the fast lane to the public cloud?
Risk, security and speed are the three elements we find small- and mid-sized enterprises are most concerned about as they ponder moving data or applications to the public cloud.
That’s why Supra ITS recently made the investment to let customers connect directly to Amazon Web Services (AWS) using AWS Direct Connect and to Microsoft Azure using ExpressRoute. These “fast lanes” to two major public cloud platforms are being offered at no extra cost for our customers as part of their managed hybrid cloud that’s already managed by us.

Selection and Security
As major cloud vendors such as Amazon, Microsoft, Oracle and Google expand their footprint on Canadian soil, we’re seeing that interested customers want flexibility – they’re not picking only one vendor. Rather, they’re using multiple cloud platforms depending on the data or the workload. For example, AWS is popular for elastic storage, while Microsoft Azure’s appeal is the ability to run AWS workloads. At the same time, customers are continuing to maintain their own private clouds, either on-premise or managed by someone else. Most likely, they are combining all three in a hybrid model.
The fact that the major public cloud players are opening Canadian facilities means they’re addressing the data sovereignty issue that keeps many organizations from embracing public cloud. Now they can be assured their data stays in Canada, whether it’s on the move or being stored. Our part of the equation is that we have Tier 3 data centres in Canada that connect to these cloud platforms. We’ll soon make available similar direct connections to Oracle and Google public cloud infrastructure.
The Last Piece of the Public Cloud Puzzle
Offering direct connections to Amazon using AWS Direct Connect and to Microsoft Azure using ExpressRoute is the last piece of the puzzle that address the risk, security and speed. These direct, secure connections to major public cloud platforms are part of Supra ITS’ overall commitment to helping customers be “public cloud neutral.” It enables our customers to embrace a true hybrid cloud model that is fast and secure because data is not being transferred over the public internet.
Reduced latency and improved performance, of course, are the obvious benefits of a direct connection to the public cloud. But in this era of frequent data breaches and increased privacy regulation, security can be a deal breaker when companies consider moving to AWS or Azure. By putting in place these fast lanes to the public cloud, combined with our existing end-to-end security that spans our customers’ on-premise IT infrastructure, the public cloud services and our own data centres, we’re able to mitigate the risk of public cloud adoption.
Set-up costs for the connections are normally included as part of transition services for Supra ITS’ managed IT customers, and the ongoing costs are included for those customers where we manage their private and public cloud. Other AWS and Azure costs are extra and depend upon the usage.
A Partner for Public Cloud Success
Cloud computing is no longer the future, it’s reality. As noted by research firm InfoTech, there’s been lots of hype about cloud, but the adoption trends are real, and Amazon Web Services and Microsoft Azure are leading the charge. At the same time, private clouds – both — on-premises and in hosted services – continue to grow. This presents an opportunity to transform IT to be an effective broker of services from the hybrid cloud.
At Supra ITS, we see our role as being a guide and resource for small- and mid-sized enterprises that are looking at how best to incorporate public cloud into their overall cloud strategy, whether it’s Amazon, Microsoft, Google or Oracle. Our neutrality enables customers to combine their on-premise, private cloud and public cloud deployments to fully take advantage of the full benefits of a managed hybrid cloud model.
- March 30, 2016
- Catagory Managed IT Services
2016 – Trends of Managed IT Services

And so, the need of the hour is a third party service provider which will support, manage and monitor your technology infrastructure. These companies go to great lengths to make your business flourish by offering you Managed IT Services that will help your business in the long run. Following a strategic plan, they install the most contemporary technology and the latest software and tools which help you stay ahead of your competitors in the domain.
Armed with the extensive know-how of the domain, they offer you excellentIT Managed Services that are highly advanced. Being a pro in all the sections makes them capable of handling network, hardware, exchange server, software and even repair, for that matter. By offering you round-the-clock assistance, they make sure that your IT setup doesn’t have to face any technical snags, making your business operations extremely smooth. Apart from this, they also keep a back up of all your data in place, in case of a disaster when recovery is not an option.
In the modern IT setup, a Managed Service Provider acts like an added advantage instead of just being a cost-effective alternative to the in-house IT team. By conducting an extensive research on your business, they understand your business requirements properly. Then after consulting you, they will come up with some customized options, exclusively made to fit your business model. Walking hand in hand with technology, they constantly upgrade your tools and software, which gives you a competitive edge in the industry.
Assuring you of the quality, these firms offer you safe and secure Managed IT solutions, which are otherwise too complex to handle. By organizing your business operations, they take everything under their control and monitor your business with hawk eyed scrutiny. Also, they are equipped with highly advanced methods that are capable of detecting any fault in the service delivery, which they ultimately do away with. And the best part is that their service rate card is fixed, so any amount of troubleshooting on their part won’t burn a hole in your pocket. So, with no headache of IT maintenance on your mind, you can focus on your key business and work for its betterment.
Working for the constant improvement of your business, these service providers offer you excellently Managed IT Solutions that have a big role to play in your business excelling. They centralize the whole system thereby making all the data available to anyone with the authorized security code. This helps you organize your operations better by letting more than one person access the same data at the same time.




 Latest Blogs
Latest Blogs FAQ
FAQ